Virtual Private Networks. They are useful, but they can also seem daunting. As I have learned more about VPN’S from my first post, some 2 years ago, I thought we should re-vist and update.
1. What’s the first thing we do? Why install openvpn of course!
REMOTE (HOST) Configuration
sudo apt-get install openvpn
2. Now we need to generate our secret key. This is used to authenticate a remote user trying to gain access. We will use openvpn itself to generate the secret key. NOTE: Debian by default, does NOT provide a path to /usr/sbin
You can fully qualify it: /usr/sbin/openvpn
temporarily add it to the PATH variable: export PATH=$PATH:/sbin:/usr/sbin:/usr/sbin
Or just add:
export PATH=$PATH:/sbin:/usr/sbin:/usr/sbin
to .bashrc
If you add it to .bashrc, you will need to logout and back in again, so it will re-read the file.
Let’s generate that key! (The key below is named homer for the host, it can be anything)
openvpn --genkey --secret homer.key
Simple, huh?
3. Let’s move some files, and create the configuration file for openvpn.
first, let’s move our secret key file:
sudo cp homer.key /etc/openvpn/.
The period at the end, is significant. It says copy the file, right here.
4. Next is the configuration file. Using your favourite editor (nano in my case) create the
/etc/openvpn/openvpn.conf file as follows: Most of the explanations of the parameters come from here.
# Sample openvpn configuration file
# jjs June 6, 2012 V1.0
#
# annotated by Wayno April 26, 2014
#
# remote specifies the address of the server
local 192.168.1.101 5001
#local 192.168.1.101 1194
# dev tun specifies that we are using a tunnel device
dev tun
# ifconfig tells ip address for the interface
ifconfig 192.168.224.253 192.168.224.254
# and the secret key name (in /etc/openvpn)
secret homer.key
# use port 5001 (default) to connect to the vpn. This may require
# you to add this in your router.
port 5001
#port 1194
# if you want data compression
comp-lzo
# ping every 10 seconds, if no ping in 120 seconds, other side dead
keepalive 10 120
# ping timer starts after it receives a connection
ping-timer-rem
# don't recreate a virtual net interface TUN after automatic restart
persist-tun
# Don't read pre-shared static key file again after auto restart
persist-key
# user and group
user nobody
group nogroup
# after initialization, run in the background as a daemon
daemon
# append the /etc/openvpn/openvpn.log
log-append openvpn.log
5. Restart openvpn
sudo service openvpn restart
If you check /etc/openvpn/openvpn.log you will get something like this:
sudo cat openvpn.log
Tue Jun 24 20:00:39 2014 OpenVPN 2.3.2 x86_64-pc-linux-gnu [SSL (OpenSSL)] [LZO] [EPOLL] [PKCS11] [eurephia] [MH] [IPv6] built on Feb 4 2014
Tue Jun 24 20:00:39 2014 TUN/TAP device tun0 opened
Tue Jun 24 20:00:39 2014 do_ifconfig, tt->ipv6=0, tt->did_ifconfig_ipv6_setup=0
Tue Jun 24 20:00:39 2014 /sbin/ip link set dev tun0 up mtu 1500
Tue Jun 24 20:00:39 2014 /sbin/ip addr add dev tun0 local 192.168.224.253 peer 192.168.224.253
Tue Jun 24 20:00:39 2014 GID set to nogroup
Tue Jun 24 20:00:39 2014 UID set to nobody
Tue Jun 24 20:00:39 2014 UDPv4 link local (bound): [AF_INET]192.168.1.101:5001
Tue Jun 24 20:00:39 2014 UDPv4 link remote: [undef]
Tue Jun 24 20:00:44 2014 Peer Connection Initiated with [AF_INET]192.168.1.103:5001
Tue Jun 24 20:00:45 2014 Initialization Sequence Completed
6. Let’s see if it works?
ping -c 5 192.168.224.253
PING 192.168.224.253 (192.168.224.253) 56(84) bytes of data.
64 bytes from 192.168.224.253: icmp_req=1 ttl=64 time=0.033 ms
64 bytes from 192.168.224.253: icmp_req=2 ttl=64 time=0.041 ms
64 bytes from 192.168.224.253: icmp_req=3 ttl=64 time=0.030 ms
64 bytes from 192.168.224.253: icmp_req=4 ttl=64 time=0.041 ms
64 bytes from 192.168.224.253: icmp_req=5 ttl=64 time=0.040 ms
— 192.168.224.253 ping statistics —
5 packets transmitted, 5 received, 0% packet loss, time 3999ms
rtt min/avg/max/mdev = 0.030/0.037/0.041/0.004 ms
==================
1. Now the CLIENT configuration /etc/openvpn/client.conf:
#
# openvpn CLIENT configuration
#
# V1.0 by Wayno April 26, 2014
# remote specifies the ip address of the remote (host) openvpn
remote 192.168.1.101
# dev tun specifies that we are using a tunnel device
dev tun
# ifconfig tells ip address for the interface
# NOTE that the ifconfig ip's are BACKWARD from the host
ifconfig 192.168.224.254 192.168.224.253
# The name of the secret key we generated (it could be anyname)
secret homer.key
# use port 5001 (note you may need to open this up in your router
# and make sure it points to the remote (host))
port 5001
# if you want data compression
comp-lzo
# ping every 10 seconds, if no ping in 60 seconds, other side dead
keepalive 10 60
# ping timer starts after it receives a connection
ping-timer-rem
# don't recreate a virtual net interface TUN after automatic restart
persist-tun
# Don't read pre-shared static key file again after auto restart
persist-key
#user and group
user nobody
group nogroup
# after initialization, run in the background as a daemon
daemon
log-append openvpn.log
2. Ensure you copy the secret key over to the /etc/openvpn on the client side. This assumes the key is already in your home folder
sudo cp ~/homer.key .
Note that the period (.) at the end IS significant.
3. And your output should look something like this:
sudo cat openvpn.log
Tue Jun 24 20:20:27 2014 OpenVPN 2.2.1 x86_64-linux-gnu [SSL] [LZO2] [EPOLL] [PKCS11] [eurephia] [MH] [PF_INET6] [IPv6 payload 20110424-2 (2.2RC2)] built on Jun 18 2013
Tue Jun 24 20:20:27 2014 NOTE: OpenVPN 2.1 requires ‘–script-security 2’ or higher to call user-defined scripts or executables
Tue Jun 24 20:20:27 2014 LZO compression initialized
Tue Jun 24 20:20:27 2014 TUN/TAP device tun0 opened
Tue Jun 24 20:20:27 2014 do_ifconfig, tt->ipv6=0, tt->did_ifconfig_ipv6_setup=0
Tue Jun 24 20:20:27 2014 /sbin/ifconfig tun0 192.168.224.254 pointopoint 192.168.224.253 mtu 1500
Tue Jun 24 20:20:27 2014 GID set to nogroup
Tue Jun 24 20:20:27 2014 UID set to nobody
Tue Jun 24 20:20:27 2014 UDPv4 link local (bound): [undef]
Tue Jun 24 20:20:27 2014 UDPv4 link remote: [AF_INET]192.168.1.101:5001
Tue Jun 24 20:20:27 2014 Peer Connection Initiated with [AF_INET]192.168.1.101:5001
Tue Jun 24 20:20:28 2014 Initialization Sequence Completed
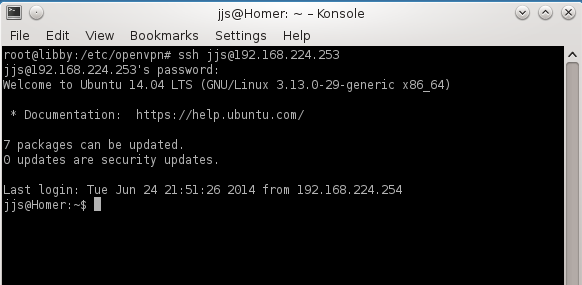
3. ssh into the vpn
nwayno@Willy:~$ ssh 192.168.224.253
nwayno@192.168.224.253’s password:
Welcome to Ubuntu 14.04 LTS (GNU/Linux 3.13.0-29-generic x86_64)
* Documentation: https://help.ubuntu.com/
Last login: Tue Jun 24 20:40:04 2014 from 192.168.224.253
nwayno@Homer:~$